Protecting rail networks: Securing mainline automatic train operation against threats
Posted: 2 March 2020 | Karl King, Lloyd Tobin | No comments yet
Karl King and Lloyd Tobin of Frazer-Nash Consultancy outline how an in-depth multi-layered approach will be needed to deliver security to automatic train operation on mainline railways.


Automatic Train Operation (ATO) is used to drive trains, with little or no human intervention, between authorised fixed points, such as stations. It uses both wired and wireless communications systems to transfer essential command and control data to, and from, rail infrastructure and the train’s on-board systems. But, with newspapers featuring near-daily stories of data breaches and cyber-attacks, how safe is ATO against these types of threat? And could these threats put the mainline railway at risk?
Whilst ATO is not currently in widespread use on mainline rail networks around the world, it is extensively used on metro railways and its implementation is likely to grow in line with increasing investment in rail networks.
Whilst ATO is not currently in widespread use on mainline rail networks around the world, it is extensively used on metro railways and its implementation is likely to grow in line with increasing investment in rail networks. There are plans for it to be adopted on areas of London’s Thameslink service and, in Mexico, a fully automated mainline railway is being developed. In the UK, where a range of rolling stock are operated, each with a different braking profile and operational characteristics, ATO currently tends to be limited to isolated lines with single stock types. As its adoption increases, however, it is essential that comprehensive security assurance is in place, to enable the constant exchange of high integrity safety- and mission-critical data between the ATO and the safety-critical Automatic Train Protection (ATP) system, as well as the Automatic Train Supervision (ATS) system responsible for train regulation.
Identifying the risk
Technologies are continuing to advance, and railways are becoming more and more digitalised, leading to the inevitable rise of new security issues for operators. The transfer of data between a train’s safety critical systems, in particular, is a potential target for hackers. Data can be subject to a ‘man in the middle attack’ – when a third-party intercepts data during its transmission between the sender and the recipient – resulting in the information being changed, delayed, or even prevented from reaching its destination.
ATO, with its assets geographically dispersed both on trains and throughout route infrastructure, and with its interconnectivity with other systems, has an increased threat surface available, making it potentially vulnerable to cyber-attack. As it transfers high-resolution, real-time train determination information between the wayside, the train and the control centre, it is essential to ensure this vital data remains secure. Unfortunately, preparation for cyber secure communication throughout the rail network is far from achieving an ideal level of maturity.
Communications Based Train Control (CBTC) systems have three key elements. The ATS has a physical (wired) interface to the infrastructure element of the safety-critical Automatic Train Protection (ATP) system, which regulates trains around the network by ensuring points are set correctly, and that trains do not collide with each other. The ATP infrastructure system connects to the points and to train detection equipment – determining where trains are situated on the network, and to where they can safely move – then transmits this data wirelessly to each train’s on-board ATP system. The train’s on-board ATP system interprets this data to determine how far it should travel, and at what speed; passing this information via a wired connection to its ATO system. Other key information, such as the next scheduled station stop, is passed wirelessly to the on-board ATO system by the ATS.
Taking a ‘defence in-depth’ approach to security
With this level of threat, mainline operators need to ensure they take a multi-layered, ‘defence in-depth’ approach to the security of their systems. Multi-layered security covers organisations’ prevention, detection and response towards their infrastructure (networks, hardware, software and applications), people (training and insider threat) and processes (the standards and legislation), thereby tightening security, reducing vulnerabilities and providing intentional redundancy. Frazer-Nash has developed a holistic approach that considers not only hardware and software technologies, information and data storage and exchange, and the standards and legislative requirements, but also the security of the physical environment and the organisational culture, including people.
Mainline railways’ level of maturity in physical security is already well-advanced, as protecting access is both a safety and an operational issue. To protect digital assets, however, it is essential that physical access to critical digital infrastructure is controlled, ensuring that only those who have a business need have access. From a technical viewpoint, network diagrams must be kept up to date, with all potential ingress and egress points on the system identified, including those accessed via the cloud. This allows the network to be monitored for unusual activity, and for attempts to gain remote access with, or without, the necessary permissions to be flagged-up. Consideration must also be given to third-party supply chain access, with specific information shared as an output while restricting further levels of entry to a system.
Granting and revoking access to a railway’s critical systems – whether to internal or external stakeholders – should be subject to a rigorously applied, formally documented process.
Granting and revoking access to a railway’s critical systems – whether to internal or external stakeholders – should be subject to a rigorously applied, formally documented process. All those involved in this process must recognise its importance, and the necessity of applying it to protect vital assets. Operators should also ensure that those with privileged access, such as administrator rights, are subject to an appropriate level of background security vetting.
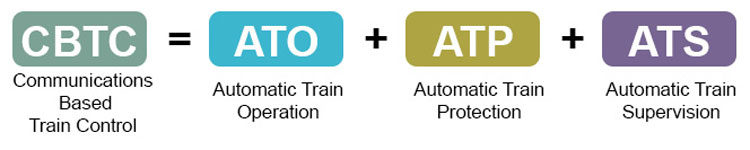

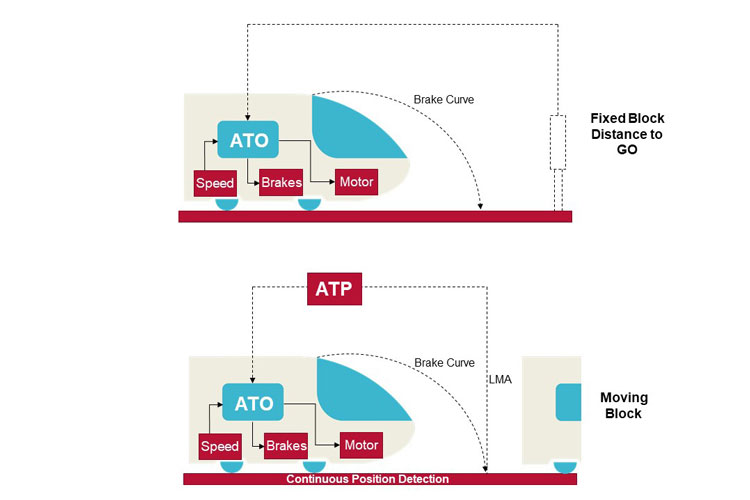

Communications Based Train Control (CBTC). Credit: Frazer-Nash Consultancy Ltd.
People and protection
Taking a defence-in-depth approach, however, goes beyond the technical. Organisations must create a culture that recognises the vital role of security in both the ‘virtual’ and ‘real’ worlds, and this culture must be backed up with robust, tested processes and procedures. In the physical environment, this might include ensuring staff display visible identification at all times, authenticating visitors and challenging potential intruders. Ongoing training of people is key to embedding a culture of awareness: When people understand how systems work, and their potential vulnerabilities, they can better protect them.
By understanding how their actions can open the door to a malicious attack, staff can avoid being a potential ‘insider threat’. Insider threats are not always the result of malicious acts by employees – as when a Canadian Pacific Railway employee accessed core switches within its network, affecting data flows and deleting and changing passwords, forcing a systems outage. Many more issues are caused by ‘unwitting’ or ‘well-intentioned’ inside threat actors, due to a lack of knowledge or understanding. For example, people may implement ‘workarounds’ to solve a work-related problem without realising that their actions have the potential to compromise security. Frazer-Nash’s human factors experts help organisations to establish a risk profile of their human insider threat, by identifying the underlying reasons and psychological motivations behind an individual’s behaviour.

Control Command and Signalling Upgrades. Credit: Frazer-Nash Consultancy Ltd.
Looking to the future
Rail operators can never ensure their systems are entirely future-proof, but will need to be forward thinking, constantly monitoring and auditing how well protected their systems are.
While a multi-layered, defence-in-depth approach can deliver assurance for current systems, ensuring the continuation of this security must be an ongoing process. At present, for example, ATO has a direct interface to the safety-critical ATP. This is not perceived as an issue, due to the one-way nature of the data exchange. However, with modern communications developing at pace, it is not beyond the realms of possibility that new technologies could enable this one-way access to be reversed. The evolution and adoption of quantum computing is also likely to change how information is transferred, and many of the algorithms and encryption currently in use could become defunct. Cyber-attackers will continue to evolve their capabilities to adapt to these technological advances, meaning communication standards previously considered secure are likely to become insecure over a relatively short period. Rail operators can never ensure their systems are entirely future-proof, but will need to be forward thinking, constantly monitoring and auditing how well protected their systems are.
Worst-case scenario?
So, what could happen if a cyber-attacker gained access to the ATO system? ATO itself is not usually classed as a safety-critical system: If there is a problem, a train running under ATO will usually travel to the next safe stopping place or will be prevented from operating by the ATP if it attempts to overstep its authority. The most likely consequence of a cyber-attack on the ATO, therefore, would be network disruption, with trains taken out of service or unable to move. However, ATO relies on the ATP system, so if hackers were able to access the ATP via ATO this could lead to more complex threats to rail safety. An attack on the ATP might override the safety functions of the train, allowing it to bypass protection points or accelerate towards buffer systems.
ATO and ATP derive some protection, as they use little to no Commercial Off The Shelf (COTS) software. Their software is generally bespoke, and operated on an isolated network. However, as there can be ‘gateways’ between safety-critical and non-safety-critical elements, if systems aren’t segmented, a successful hacker could move internally across operating systems – for example, from signalling to infrastructure. Furthermore, ‘security by obscurity’ is well-recognised as a fallacy in the cyber-security industry; bespoke systems are generally much less subject to scrutiny by the security research community, and hence vulnerabilities are less likely to be discovered and fixed.
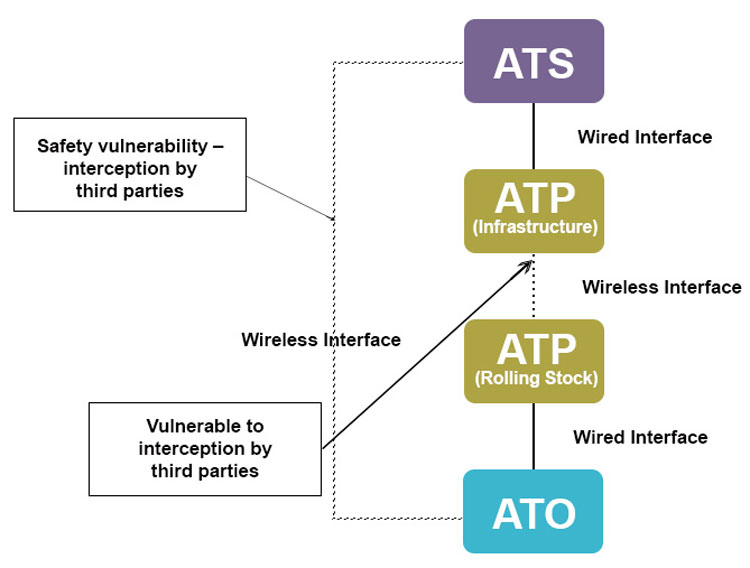

Threats to the System. Credit: Frazer-Nash Consultancy Ltd.
Learning from others
While the cyber-threat to ATO on the mainline railway remains limited at present, there is no guarantee that this will remain the case in the future. One key challenge in the UK is that, despite the number of different types of rail company involved in train operation – infrastructure, freight, passenger and others – there is no overarching systems authority with responsibility for oversight of cyber-security in rail. This may change, following the recommendations made in the Williams Report, and would provide a level of guidance and best practice that would greatly benefit rail operators concerned about cyber-threats. The rail industry could then take the opportunity to adopt standards for data transferred from similar critical transport sectors, with a greater cyber and digital maturity. In the meantime, Frazer-Nash along with its joint venture partner, Context Information Security, is working to develop a body of guidance material for the Rail Delivery Group (RDG), which is then intended to be promulgated to the industry.
While the cyber-threat to ATO on the mainline railway remains limited at present, there is no guarantee that this will remain the case in the future.
Frazer-Nash has been delivering solutions to the rail sector for many years, which draw upon best practice from diverse industries – from power generation to aerospace – and can help mainline operators to identify and benefit from the lessons learned from transportation systems further along the ATO route, such as the metro industry. Alongside this, operators must ensure that their supply chain is also secure, encouraging suppliers to achieve accreditation, such as Cyber Essentials Plus. Railways have seen many regulations introduced to protect operational safety – perhaps as cyber-threats to mainline railways increase, we will see regulations brought in to protect digital safety too.




Stay Connected with Global Railway Review — Subscribe for Free!
Get exclusive access to the latest rail industry insights from Global Railway Review — all tailored to your interests.
✅ Expert-Led Webinars – Gain insights from global industry leaders
✅ Weekly News & Reports – Rail project updates, thought leadership, and exclusive interviews
✅ Partner Innovations – Discover cutting-edge rail technologies
✅ Print/Digital Magazine – Enjoy two in-depth issues per year, packed with expert content
Choose the updates that matter most to you. Sign up now to stay informed, inspired, and connected — all for free!
Thank you for being part of our community. Let’s keep shaping the future of rail together!
Related topics
Automatic Train Operation/Autonomous Train Control (ATO/ATC), Big Data, Communications Based Train Control (CBTC), Consultancy, Cyber-Security, Digitalisation, Safety